Business Email Compromise (BEC): A Growing Cybersecurity Crisis for Canadian Businesses
Brief: Business Email Compromise (BEC) has emerged as one of the most financially damaging cyber security threats facing Canadian businesses today. With cybercriminals exploiting email systems using sophisticated social engineering, the cost of a single breach can reach millions of dollars. This article explores how BEC works, the evolving threat landscape in Canada, and what senior leaders must do to protect their organisations and reputations.
“Canadian businesses can no longer afford to treat cyber security as a technical afterthought. Business Email Compromise isn’t just an IT risk—it’s an executive, reputational, and financial risk that demands a boardroom response.” — F12.net Cybersecurity Leadership Team
Understanding the Threat Landscape: What is Business Email Compromise (BEC)?
Business Email Compromise (BEC) attacks have rapidly become one of the most pervasive and financially destructive cyber security threats for Canadian businesses. As digital communication becomes foundational to how organisations operate, threat actors have zeroed in on email systems—exploiting them with advanced, targeted deception techniques. Sophisticated BEC scams rely on trust, using authentic-looking messages to manipulate staff and transfer funds, expose data, or establish long-term, covert access to sensitive business processes.
An in-depth review of more than 1,000 recent BEC incidents—spanning industries from professional services to manufacturing—reveals the most common tactics and why Canadian businesses are uniquely exposed. The conclusion? BEC isn’t an IT problem; it’s a business continuity and leadership challenge.
The Financial and Operational Impact of BEC in Canada
According to the FBI’s Internet Crime Complaint Center (IC3), BEC scams accounted for over $2.4 billion USD in reported losses in a single year[source]. Canadian businesses are not immune. A single compromised account can lead to direct wire fraud, payroll redirection, exposure of customer information, operational disruption, reputational harm, and—if personal or health data is involved—costly compliance breaches under PIPEDA or provincial privacy laws. Once funds leave the country, recovery is rare.
What’s particularly dangerous about BEC is its stealth. Unlike ransomware, BEC attacks often go undetected for weeks or months, quietly siphoning funds or data. Canadian businesses—especially those in essential services—are particularly attractive targets due to large transaction volumes, supply chain relationships, and the implicit trust placed in executive and finance communications.
BEC vs. Ransomware: The Hidden Menace
Where ransomware disrupts business operations loudly and immediately, Business Email Compromise is insidious. Attackers study internal hierarchies, impersonate executives or trusted suppliers, and blend into daily business communications. By the time a fraud is discovered—whether it’s a redirected invoice, payroll scam, or data theft—the damage is often done, and the financial loss irrecoverable.
How Business Email Compromise Attacks Work
Most BEC attacks begin with a single compromised email account, often gained through phishing or weak passwords. Once inside, cybercriminals study communication patterns and insert themselves into legitimate threads—redirecting payments, manipulating invoices, or harvesting credentials to deepen their access. The core objectives typically include:
- Funds transfer fraud—redirecting payments or payroll
- Credential harvesting—for broader account compromise
- Data theft—extracting sensitive business or customer records
- Persistence—setting up rules for long-term, covert access
Phishing is the primary entry point in over 90% of BEC incidents. Attackers increasingly use spear phishing, referencing real projects, executives, and vendors. Sophistication matters—LinkedIn, company websites, and public records all become research tools for the adversary.
What 1,000 BEC Incidents Reveal About the Canadian Threat Landscape
From 2020 through 2024, reported Business Email Compromise incidents in Canada have climbed year-over-year. The initial spike in 2020–2021 mirrored the sudden move to remote work, exposing new cloud and personal device vulnerabilities. By 2022–2023, phishing-driven BEC attacks grew more targeted, often bypassing basic cyber security controls. And in 2024, the highest volume of incidents yet coincided with tougher regulatory oversight, mandatory breach reporting, and better detection tools.
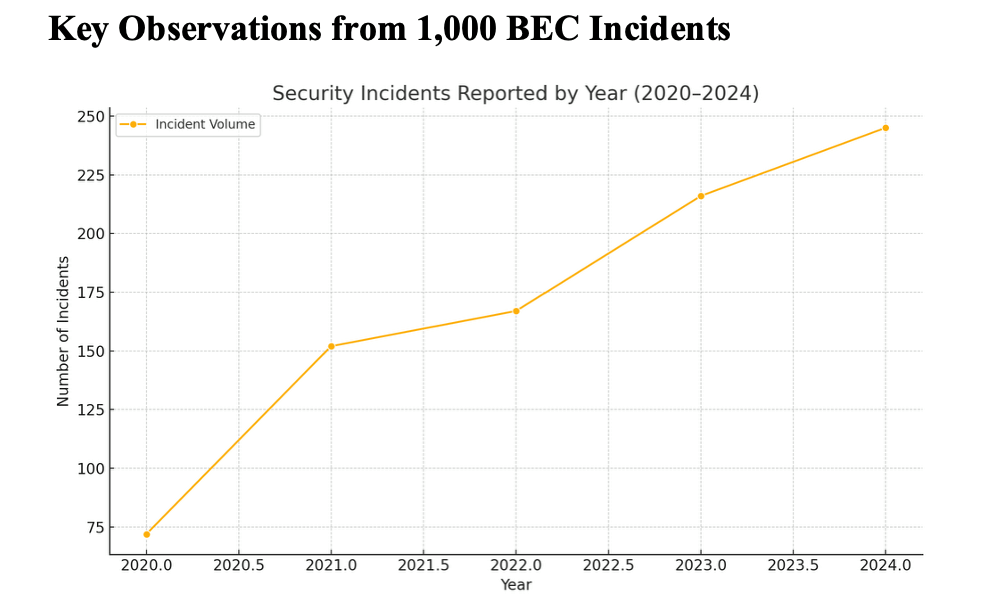
Figure: The number of Business Email Compromise (BEC) incidents reported by Canadian businesses continues to climb year-over-year, underlining the urgent need for robust cybersecurity measures and executive oversight. Source: Analysis of 1,000 BEC incidents, 2020–2024.
Yet the upward curve tells a story: while detection is improving, adversaries are innovating faster. Proactive, intelligence-driven cyber security—not reactive compliance—must be the new standard for Canadian business.
Common BEC Attack Techniques Targeting Canadian Businesses
Phishing and Social Engineering
Spear phishing—using authentic details and real contacts—is now the norm. Finance and HR teams, as well as executives, are prime targets. Threat actors spend time crafting messages that mirror legitimate business communication, making detection a challenge even for vigilant employees.
Multi-Factor Authentication (MFA) Bypass
MFA is necessary but not infallible. Attackers bypass it via SIM swapping, push fatigue, or by stealing session tokens through phishing. Canadian businesses relying on SMS or call-based MFA should urgently review their practices and shift to phishing-resistant methods like FIDO2 keys.
Email Rule and Filter Abuse
Attackers establish persistence by creating mailbox rules that delete or forward critical emails. Without specific alerting, these rules can go unnoticed for months, giving criminals ongoing access to sensitive business communications.
Abuse of Third-Party Apps
OAuth application abuse is rising. Attackers grant rogue apps persistent access to business mail, often bypassing password resets. Regular audits of Microsoft 365 and Google Workspace app permissions are non-negotiable.
International IP and VPN Use
Many BEC attacks are launched from international locations, using VPNs or anonymisation tools to evade geo-blocking. Without proactive monitoring and geofencing, businesses are exposed.
Delayed Detection
The average time before BEC discovery remains high—between 6 and 30 days. Most incidents are reported not by the business itself, but by third parties. This underlines the need for automated, 24/7 monitoring and rapid response protocols.
Human Behaviour as a Risk Amplifier
Social engineering remains at the heart of BEC. Attackers exploit urgency, trust, and authority. No amount of technical control replaces continuous employee training and leadership engagement in cyber security culture.
BEC in Action: Recent Case Studies from Canadian Businesses
Non-Profit: Attackers gained access to SharePoint financial folders and manipulated email conversations, exploiting identity misconfigurations.
Architectural Firm: Sophisticated phishing bypassed MFA, abused mail rules, and spread internally.
Food Distributor: Covert use of Outlook rules concealed ongoing phishing and financial fraud.
Home Builder: Payroll fraud succeeded due to social engineering and human error, not technical failure.
Oil & Gas: Outdated password policies and over-permissioned apps enabled large-scale BEC.
Defending Canadian Businesses Against BEC: Strategic Recommendations
- Strengthen Email Protection: Use advanced threat filtering, Safe Links, Safe Attachments, and anti-impersonation policies.
- Enforce Secure MFA: Disable SMS/call MFA, mandate app-based or FIDO2 authentication, and monitor for session persistence abuse.
- Conditional Access and Geo-Restrictions: Enforce location-based access controls and device compliance checks.
- 24/7 Threat Monitoring (MDR): Invest in Managed Detection and Response for continuous oversight of email, identity, and endpoints.
- Monitor Application Permissions: Regularly audit OAuth apps, restrict admin consent, and block legacy authentication.
- Security Awareness Training: Implement ongoing phishing simulations, including executives and finance staff.
- Limit External Sharing: Restrict external file access in SharePoint/OneDrive, audit regularly, and disable anonymous sharing.
- Endpoint Detection and Response (EDR): Deploy and monitor EDR solutions across all devices.
- Dark Web Monitoring: Proactively scan for leaked credentials and automate response protocols.
- Reliable Backups: Ensure business data is backed up, tested, and aligns with retention policies.
- Secure Email Infrastructure: Deploy SPF, DKIM, and DMARC to stop spoofing and fraud at the source.
Cyber security is no longer just a technology function; it’s a strategic imperative for every Canadian business. Board-level engagement and cross-functional collaboration—across finance, HR, operations, and legal—are essential to build resilience against BEC and all forms of digital risk.
Building a Cybersecurity Culture: From Compliance to Commitment
Cyber security culture isn’t about checking boxes. It’s about leadership, shared responsibility, and proactive communication. Senior executives must model strong authentication, participate in security exercises, and talk about cyber security as a strategic priority, not a technical side issue.
Tabletop exercises should involve every department, surfacing policy blind spots and strengthening organisational muscle memory. Post-incident reviews—conducted with transparency—turn security failures into learning opportunities and build trust across the workforce.
The result? Organisations that move faster, innovate with confidence, and build lasting trust with customers and partners.
Turn Insight Into Action: The Real Cost of Inaction
The cost of Business Email Compromise goes beyond stolen funds. It erodes trust, damages reputation, and distracts leadership from growth. Prevention—through regular training, automated monitoring, strong policies, and cross-functional engagement—is far less costly than recovery. The next breach report could name your organisation, or it could highlight your proactive leadership. In cyber security, proactivity isn’t a competitive advantage—it’s survival.
Want to learn more or need a risk assessment? Contact F12.net today to schedule a confidential cyber security review for your Canadian business. Don’t wait for the next headline—take action now.
Frequently Asked Questions about Business Email Compromise (BEC) in Canadian Businesses
- Q: What is Business Email Compromise (BEC)?
- Business Email Compromise (BEC) is a targeted form of cyber crime where attackers use email fraud, phishing, or account takeover to trick companies into transferring funds or sharing sensitive information. Bottom line: BEC uses trust and authority to bypass technical controls and directly exploit business processes.
- Q: How common are BEC attacks in Canada?
- BEC incidents have risen sharply in Canada since 2020, impacting hundreds of organisations each year and causing millions in direct financial losses. Bottom line: Every Canadian business, regardless of size or industry, is now a potential BEC target.
- Q: What makes BEC more dangerous than ransomware?
- Unlike ransomware, which is overt and often detected quickly, BEC is stealthy and can go undetected for weeks or months. Attacks often blend into normal business activity and rely on social engineering, not malware. Bottom line: The true danger of BEC is its ability to compromise your business quietly, leading to larger losses and regulatory consequences.
- Q: How do BEC attackers usually get access to business email accounts?
- Most BEC attacks begin with spear phishing, credential theft, or exploiting weak passwords and legacy authentication. Attackers may also abuse insecure multi-factor authentication methods or leverage compromised third-party applications. Bottom line: Your people, passwords, and third-party apps are the front lines—each must be secured and monitored.
- Q: What should my business do immediately if we suspect a BEC incident?
- Immediately isolate compromised accounts, alert your IT and security provider, notify your financial institution, and report the incident to law enforcement or the Canadian Centre for Cyber Security. Conduct a forensic investigation to determine the scope of the breach. Bottom line: Speed matters—quick action can prevent further losses and aid recovery.
- Q: How can Canadian businesses best protect themselves against BEC?
- Deploy layered cyber security: strong email filtering, phishing-resistant MFA, real-time monitoring, regular employee training, and executive engagement. Regularly audit permissions, monitor for unusual account behaviour, and build a culture of vigilance across all departments. Bottom line: The most resilient businesses treat cyber security as a shared leadership responsibility, not just an IT task.
- Q: Does cyber insurance cover Business Email Compromise?
- Many Canadian cyber insurance policies cover BEC, but successful claims depend on maintaining appropriate security controls, incident response procedures, and accurate reporting. Bottom line: Review your policy regularly and ensure your security posture aligns with insurer requirements—prevention is always better than relying on insurance.



